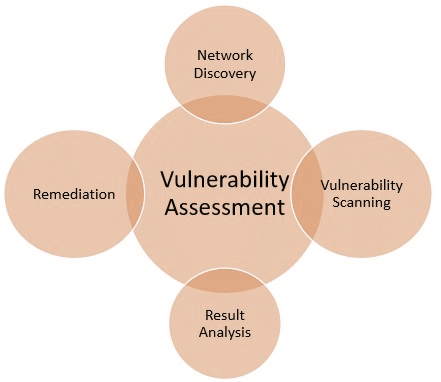
What is a Vulnerability Assessment?
It can be performed either externally to emulate an attack from the internet or remote network, or internally to emulate an attack by a malicious insider.
Once the scope of the assessment has been determined, the initial phase of testing will profile vulnerabilities in the infrastructure. When identified, vulnerabilities can be manually verified without exploitation or a full penetration test can be carried out to attempt system access or retrieval of data and personally identifiable information (PII).